Reverse Engineering a WEB API
In this blog post, I am going to explain basically how the REST API of a service can be reverse-engineered. This post is written for educational purposes and I don’t approve usage of it for unethical purposes and I do not accept any responsibility.
If we look at the ways of how we can reverse-engineer the API of the service, we may expect to reverse-engineer client-side rendering services. For example if we inspect a web site that returns data as JSON, or if network tab of inspection panel changes constantly to get a new data, we may use the data URL of it. Another point is mobile applications are generally uses JSON, instead of server-side rendering data for concerns of data usage. So, we may reverse engineer an Android APK file to reverse engineer an API.
For decompilation process, we may use the tools like Apktool and Ninjadroid. The tool called Apktool decompiles our APK to smali detailed and we can search strings and resources easily, on the other hand NinjaDroid could convert APK to JAR file, then we may use JAR file with IntelliJ IDEA or Fernflower tool to find authentication process algorithm.
The words given below can be searched inside the files of extracted folders that created by these tools to find important details:
- API
- http
- constant
- secret
- key
- auth
- authentication
- authorization
- JSON
- token
- OAUTH
- OkHttpClient
- Interceptor The related strings inside files may give us URL of the API, query examples, client-secret key and more, then we may find the algorithm for authentication on our JAR file that we converted (OkHttpClient or other HTTP client libraries may involved and/or may contain Interceptor, so searching these terms are advised), could imitate the process of authentication.
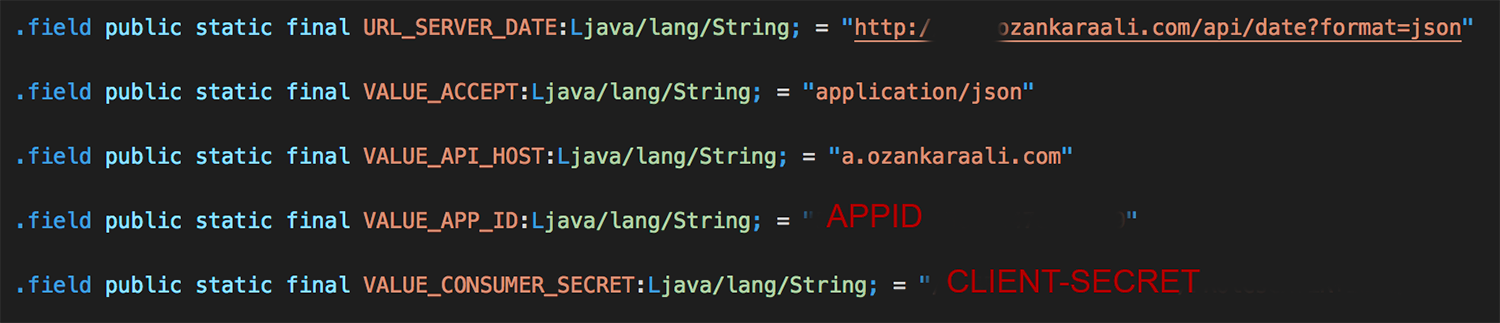
Information that we found in constants file
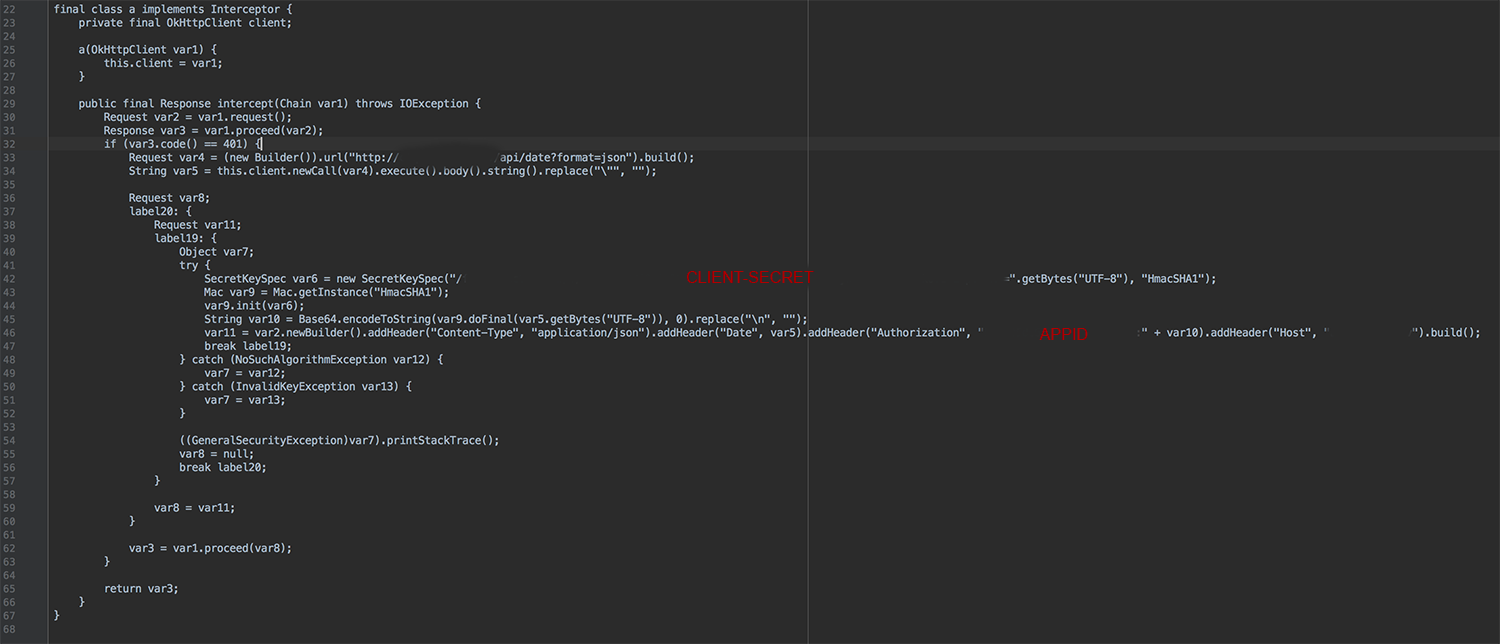
Authentication algorithm
On the other hand, network sniffing tools like Wireshark could listen our Android device (or emulator) that have sent/received data. After collecing packets from Android device, we can search API URL with CTRL-F/Command-F and selecting string search (for example api.ozankaraali.com), related packages may give the full string and example usage of query URLs (for example api.ozankaraali.com/queryURL?query=question).
With all the information we got could be used a software like [Postman] (https://www.getpostman.com/) or a programming language to create a program that queries the API that we reverse-engineered. For example the API I have is like api.ozankaraali.com/queryURL?query=question and to get response, we set-up headers that API needs (under normal circumstances, authorization process would be applied to block unauthorized access and we imitate with getting algorithm from we get from mobile application), we request with a header like this “Authorization: Bearer <Base64(CurrentDate) + ClientSecret>” (not all the same, this is a random example, other examples can be OAUTH -1 or 2-), we requested like mobile application we have and got response.
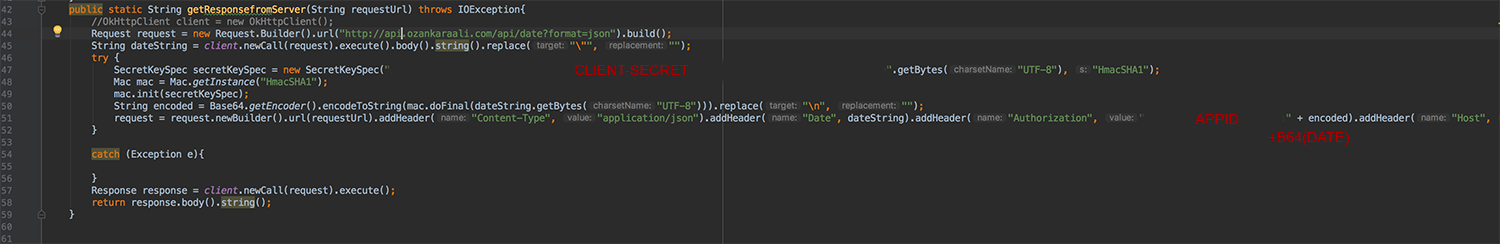
The imitation program of given above that we have written
As a result, you may use the unpublished API of a web site or a service with this way (check Terms of Service of the service to find if it is not allowed to reverse-engineered and you will not use this method for unethical work).
Note
Bu makalenin Türkçesini BURADAN okuyabilirsiniz.
You can read the Turkish version of this article HERE.